When Layer 2 Strikes Back — A Real-World ARP Attack Case from the SOC Floor
A real-world SOC case study uncovering an ARP spoofing attack on Layer 2 networks—revealing how attackers manipulate network traffic inside enterprises.
Read on HashnodeI don’t just monitor logs — I hunt threats, stop attacks, and protect what matters. Every alert is a puzzle, every anomaly a clue, and I thrive on turning chaos into clarity. With a flawless 4.0 GPA in my Master’s in Cybersecurity and a stack of industry-leading certifications, I don’t wait for attackers — I anticipate them, outthink them, and shut them down. My work is more than defense; it’s resilience in action — fortifying systems, empowering teams, and ensuring that when adversaries come knocking, they’re met with a wall they cannot breach

I see cybersecurity not as a job, but as a responsibility — a duty to stand between chaos and order. Every log, every alert, every anomaly tells a story, and I make sure that story never ends in compromise. As a blue team specialist and Master’s student in Cybersecurity at the University of Houston , I’ve built my path on protecting, detecting, and responding with precision. Armed with certifications like CySA+, PenTest+, CEH, SAL1, and Fortinet Associate, I dive deep into SIEM operations, threat hunting, incident response, and malware analysis. At Unisys Global Services, I didn’t just patch weaknesses — I engineered resilience that cut risk and strengthened enterprise defenses. My projects, from deploying Zero Trust architectures to building malware sandboxes, prove that I don’t just theorize security — I create it, test it, and harden it against real-world threats. And because defense is bigger than one person, I’ve mentored thousands, spreading the awareness that turns employees into the first line of defense. My mission is clear: anticipate the adversary, defend with purpose, and transform resilience into a lasting advantage.

Designed a safe and secure home monitoring system that can prevent accidental fire and shorting of home components.
Designed and implemented an advanced threat detection system using Splunk and Elastic Stack to monitor real-time network traffic and detect suspicious activities.
Created a website so that hospital patient’s reports can easily be uploaded without any middleman.
Designed and implemented a Zero Trust Architecture using micro-segmentation and strong identity verification mechanisms to enhance security in enterprise networks.
Built a custom malware analysis sandbox using IDA Pro, Python, and virtualization tools to analyze malware behavior and reverse engineer malicious code.
Developed a toolkit to simulate phishing, pretexting, and baiting attacks in a controlled environment to train employees on recognizing social engineering threats.
Built a self-learning SOC assistant that uses LLMs to triage alerts, auto-write reports, correlate logs, and execute automated playbooks for incident response, integrated with SIEM and SOAR platforms.
Developed a threat intel system that breaks malware into “genetic markers” (API calls, encryption patterns, etc.), maps family evolution with graph databases, and enables defenders to predict unseen malware by genetic similarity on a web dashboard.
Created a cyber range simulating full APT attack chains for offense and defense, with automated attack scripts and real-time detection mapped to MITRE ATT&CK, plus a scoring engine to track team response effectiveness.
GPA: 4.0
GPA: 3.5
EC-Council
CompTIA
CompTIA
CompTIA
CompTIA
Cisco
Cisco
Pega
Pega
EC Council
Try Hack Me
Fortinet
AWS
Achieved a perfect 4.0 GPA in the Master’s in Cybersecurity program at the University of Houston, ranking among the top performers while balancing advanced research and real-world security projects.
Spearheaded secure application development at Unisys Global Services, reducing enterprise vulnerabilities by 62%, directly improving the organization’s resilience against modern cyberattacks.
Trained and mentored 2,000+ students and professionals worldwide, delivering advanced courses and workshops in ethical hacking, network defense, and SOC operations, creating industry-ready defenders.
Designed and deployed projects such as Zero Trust Architecture, an AI-driven Threat Detection Platform, and a Custom Malware Analysis Sandbox, demonstrating the ability to innovate solutions against evolving adversaries.
Achieved 10+ elite certifications including CompTIA PenTest+, CEH, CySA+, CCNP, Fortinet Certified Associate, and SAL1, proving mastery across red team, blue team, and cloud defense disciplines.
Delivered high-impact training, published research-driven projects, and conducted live cyber defense simulations, earning recognition as a trusted voice bridging academia, industry, and the security community.
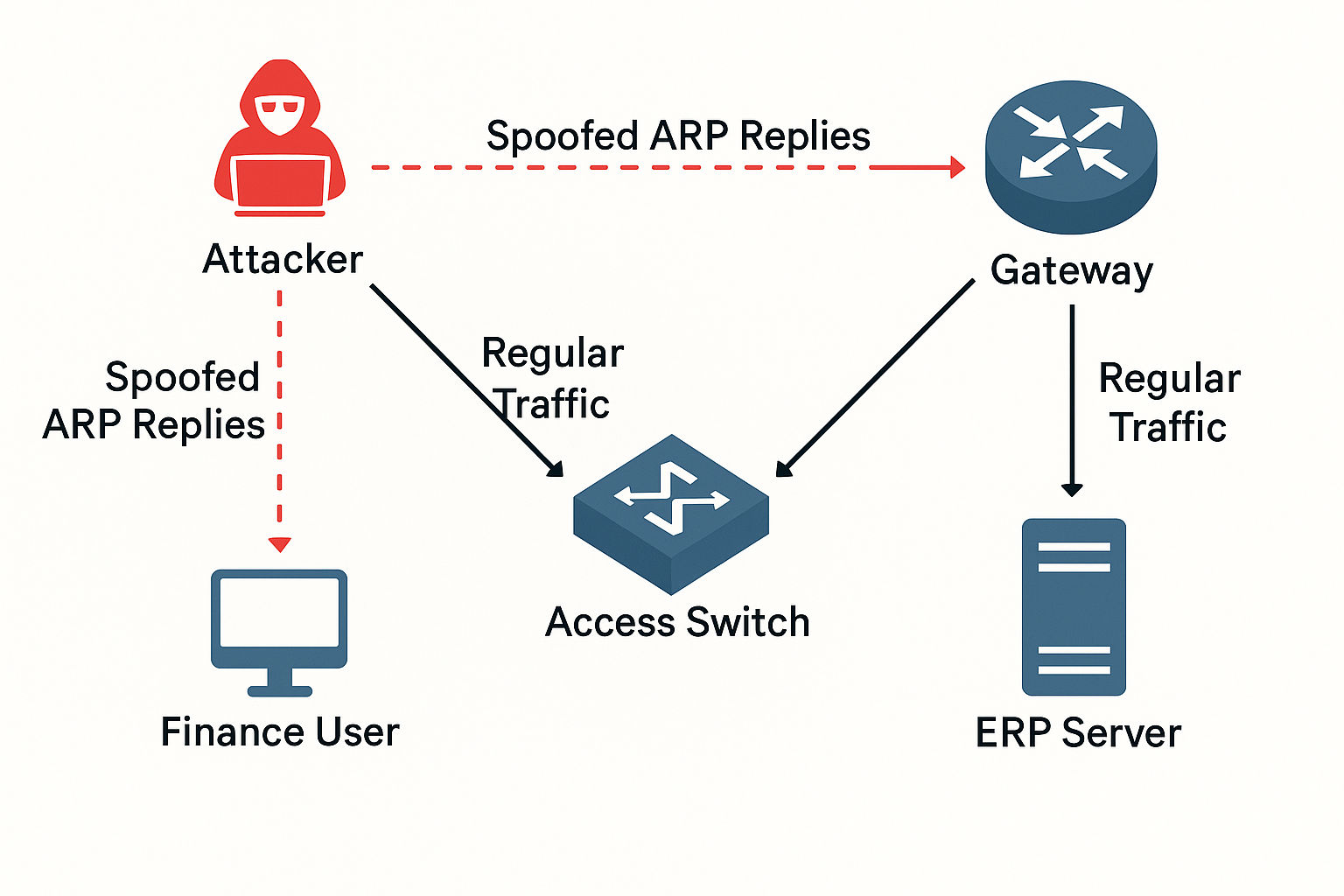
A real-world SOC case study uncovering an ARP spoofing attack on Layer 2 networks—revealing how attackers manipulate network traffic inside enterprises.
Read on Hashnode